This is continued from AWS CloudFormation: 03 - Collect logs .
Background
I want to build my software and deploy it to the web server.
What we need?
- Install CodeDeploy agent on the EC2 instances to deploy new software.
- A CodeBuild setup to build the software.
- A CodeDeploy setup to deploy the software.
- A CodePipeline setup to build and deploy the software.
How to do it?
This is what we are going to do:
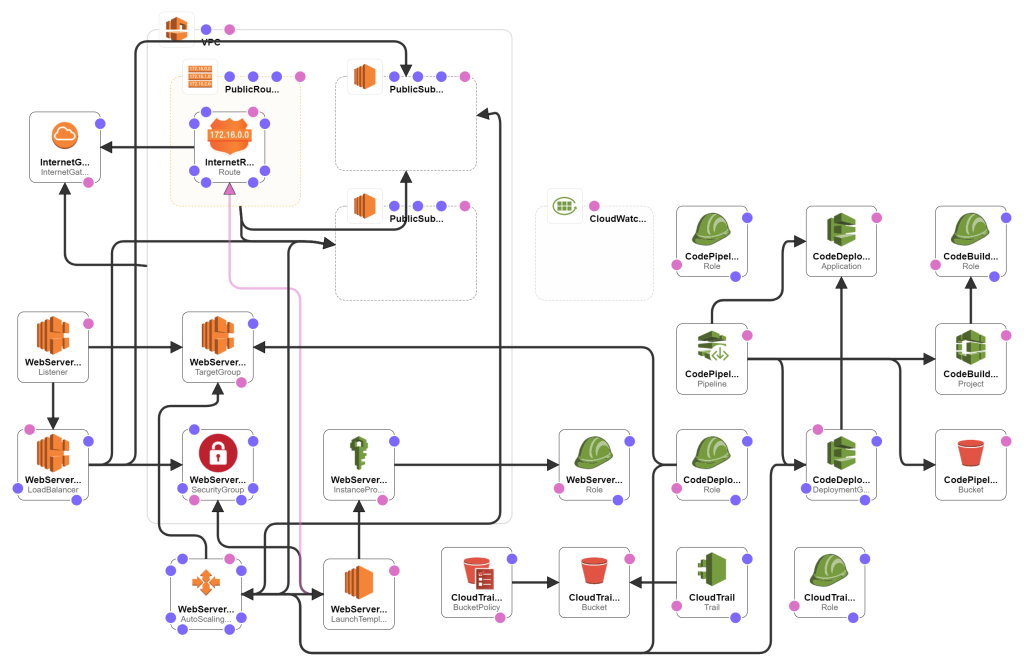
Open 03-cloudwatch-template.yaml from previous post and save as 04-codepipeline-template.yaml .
Launch Template
We will need to setup the CodeDeploy agent on the EC2 instances. Modify these resources:
| 1 |
WebServerServiceRole:
|
The IAM Policy for the EC2 instance to access the build artifacts on the S3 bucket. |
| 2 |
WebServerLaunchTemplate:
|
Add the steps to install CodeDeploy agent. |
Configure:
|
Add the configuration to allow CodeWatch agent to collect log file of CodeDeploy agent. |
Build and Deploy Pipeline
We will need to setup a pipeline to build and deploy our software. Add these resources:
| 1 |
CodePipelineBucket:
|
The S3 bucket to store the source artifacts and build artifacts. |
| 2 |
CodeBuildServiceRole:
|
The IAM Role to allow the CodeBuild project to access the S3 bucket. |
| 3 |
CodeBuildProject:
|
The CodeBuild project to build the software. |
Source:
|
The steps to build the software. | |
- mkdir scripts
|
Add a script to run before installing the software. | |
- |
|
Add a spec file so CloudDeploy agent knows how to deploy the software. | |
artifacts:
|
Tell the CodeBuild project how to pack the build artifact. | |
LogsConfig:
|
Store the build log in S3 bucket. | |
| 4 |
CodeDeployServiceRole:
|
The IAM Role to allow the CodeDeploy service to access the required resources. |
Policies:
|
It needs to access to the auto scaling group so it can manage the EC2 instances on behalf of it. | |
- Resource: "*"
|
It needs to access to the EC2 instances created by the auto scaling group so it can manipulate them. | |
- Resource: !Ref WebServerLoadBalancerTargetGroup
|
It needs to access to the load balancer so it can control the traffic when deploying. | |
- Resource: !Sub ${CodePipelineBucket.Arn}/*
|
It needs to access to the S3 bucket so it can download the build artifacts. | |
- Resource: "*"
|
And some other non-resource specific policies. | |
| 5 |
CodeDeployApplication:
|
A CodeDeploy application. |
| 6 |
CodeDeployDeploymentGroup:
|
A CodeDeploy deployment group that define how to deploy the software. |
| 7 |
CodePipelineServiceRole:
|
The IAM Role to allow the CodePipeline service to access the required resources. |
Policies:
|
It needs to use the source code connection string to pull the source code from the repository. | |
- Resource: !Sub ${CodePipelineBucket.Arn}/*
|
It needs to access to the S3 bucket. | |
- Resource: !Sub ${CodeBuildProject.Arn}
|
It needs to access to the CodeBuild project. | |
- Resource:
|
It needs to access to the CodeDeploy service. | |
| 8 |
CodePipeline:
|
This is the pipeline to buid and deploy the software. It will use the S3 bucket created earlier to store all the artifacts. |
Properties:
|
Define where is the source code. | |
- Name: Build
|
Define the build stage. | |
- Name: Deploy
|
Define the deploy stage. |
Parameters
We need to add a few parameters to know where is the source code repository. Add these parameters:
| 1 |
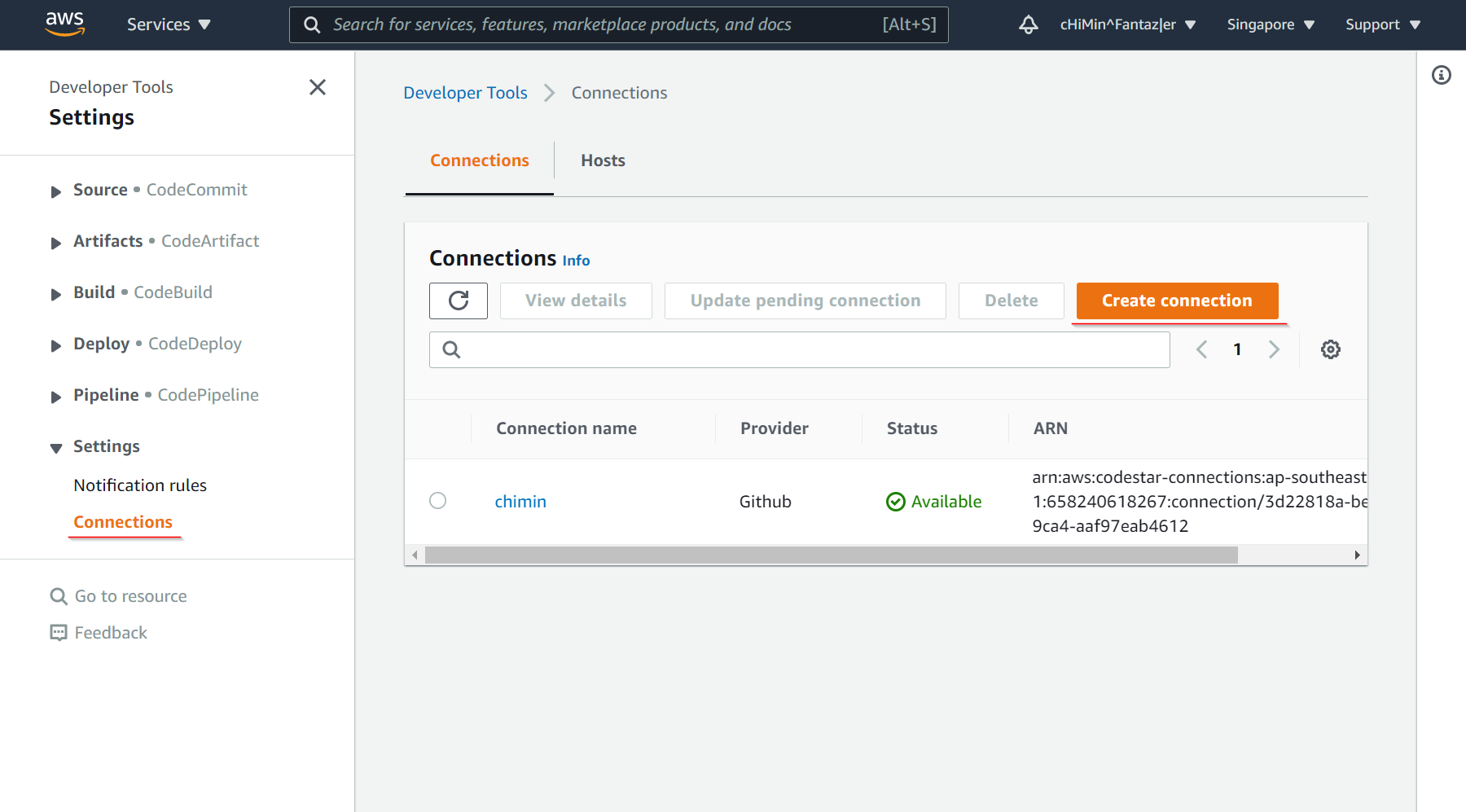
SourceCodeConnectionArn:
Type: String Default: <your source code connection> |
The source code connection string. You can create one with AWS developer tools:
|
| 2 |
SourceCodeRepository:
|
The source code repository name. |
Update the stack then you should be able to see the CodePipeline. Execute the pipeline and you should get the software built and deployed to the EC2 instances.
Next we will do AWS CloudFormation: 05 - Create a web server Docker instance .