This is continued from AWS CloudFormation: 02 - Create an auto scaling group .
Background
I want to see all the logs in a central place.
What we need?
- Install CloudWatch agent on the EC2 instances to collect logs.
- Create a S3 bucket to store the logs.
- Create a CloudWatch log group to see the logs.
How to do it?
This is what we are going to do:
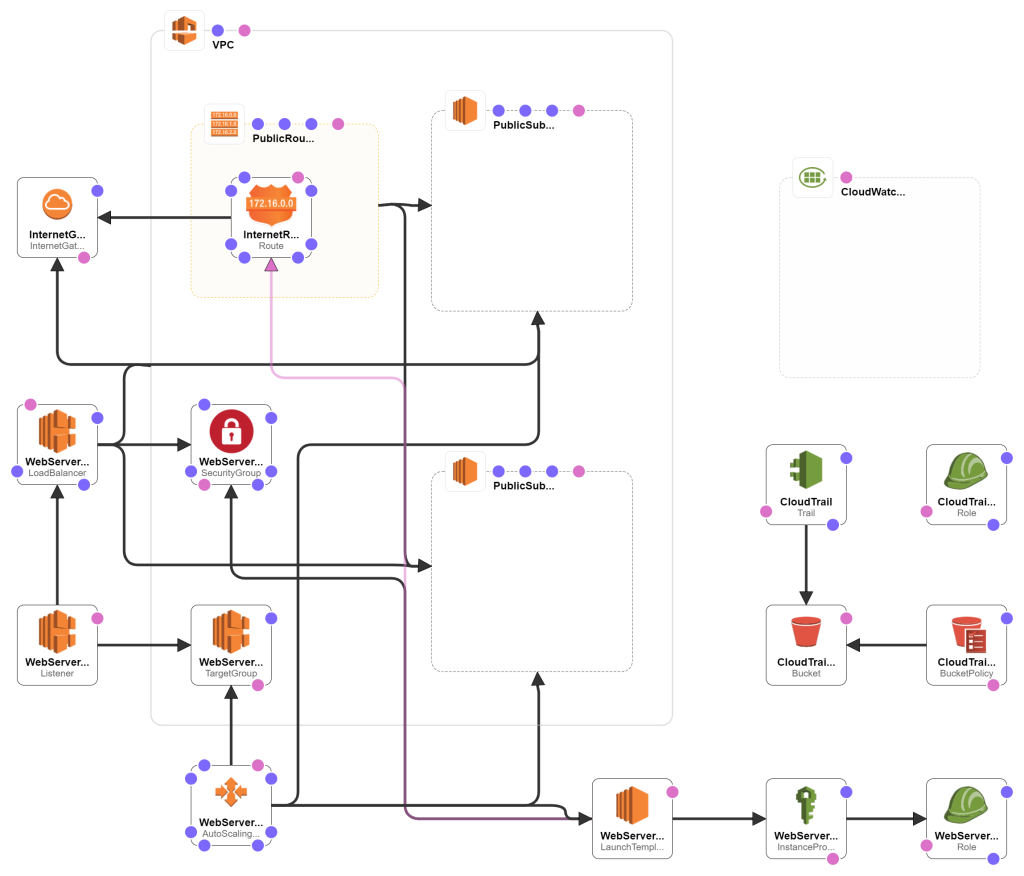
Open 02-autoscaling-template.yaml from previous post and save as 03-cloudwatch-template.yaml .
Launch Template
The EC2 instance will need to have permission to post to the CloudWatch logs. We need to attach a IAM Role to the EC2 instance. Add these to the resources:
| 1 |
WebServerServiceRole:
|
This is the IAM Role to post to the CloudWatch logs. It uses the managed policy named CloudWatchAgentServerPolicy. |
| 2 |
WebServerInstanceProfile:
|
This is the EC2 instance profile that we can attach it to the EC2 instance in the launch template. |
Modify these resources:
| 1 |
WebServerLaunchTemplate:
|
Attach the EC2 instance profile to the EC2 instance. |
UserData:
|
Change to use CloudFormation helper script to setup the EC2 instance. The details will be retrieved from the metadata defined later. | |
/opt/aws/bin/cfn-signal -e $? \
|
Signal the auto scaling group that this instance is ready so the auto scaling group doesn't need to wait indefinitely for the instance to be ready. | |
Metadata:
|
Define the config sets for the CloudFormation metadata. | |
Install:
|
Setup NGINX web server and the CloudWatch agent. | |
Configure:
|
Setup the CloudWatch agent configuration file to collect error logs from NGINX web server. | |
Start:
|
Start the NGINX web server and the CloudWatch agent. | |
| 2 |
WebServerAutoScalingGroup:
|
Change the auto scaling group to wait for the EC2 instance to be ready in 5 minutes. |
Logs
We will create the CloudWatch log group. Add this to the resources:
| 1 |
CloudWatchLogGroup:
|
The log group for CloudWatch. The log entries will be automatically deleted in 3 days. |
We can log the events in AWS to the CloudWatch log group also, for example events like AccessDenied. We can see the events directly in CloudTrail but logging them to the CloudWatch gives us more flexibility in searching the log entries. Add these to the resources:
| 1 |
CloudTrailBucket:
|
This is the S3 bucket to store the logs. |
| 2 |
CloudTrailBucketPolicy:
|
This is the S3 bucket policy that allows CloudTrail to put object in the bucket. |
| 3 |
CloudTrailServiceRole:
|
This is the IAM Role that allows CloudTrail to post log entries to the CloudWatch log group. |
| 4 |
CloudTrail:
|
This configures CloudTrail to log events to S3 bucket and CloudWatch. |
Update the stack then you should be able to see the logs in the CloudWatch. Note that it will take 5 min - 15 min before the log entries appear in both CloudTrail and CloudWatch. This is a pain in the ass.
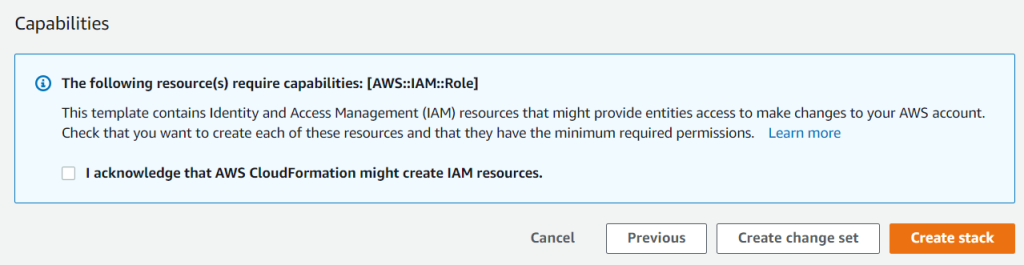
When the CloudFormation contains IAM Role resources, we need to specifically acknowledge it before the AWS can create the resources.
When you delete the stack, it will not allow you to do so also if your S3 bucket is not empty.
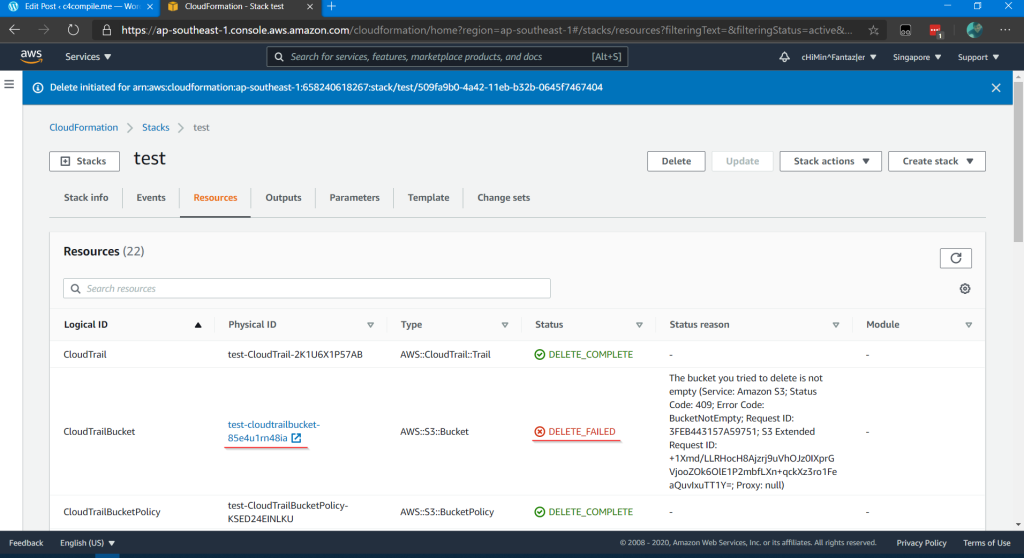
You will have to manually empty the S3 bucket and delete the stack again.
Next we will do AWS CloudFormation: 04 - Build and deploy pipeline .