This is continued from AWS CloudFormation: 06 - Collect logs from Docker instance .
Background
I want to build my software and deploy it to the Docker instance.
What we need?
- A Docker registry to store the Docker images.
- A CodeBuild setup to build the software.
- A CodeDeploy setup to deploy the software.
- A CodePipeline setup to build and deploy the software.
How to do it?
This is what we are going to do:
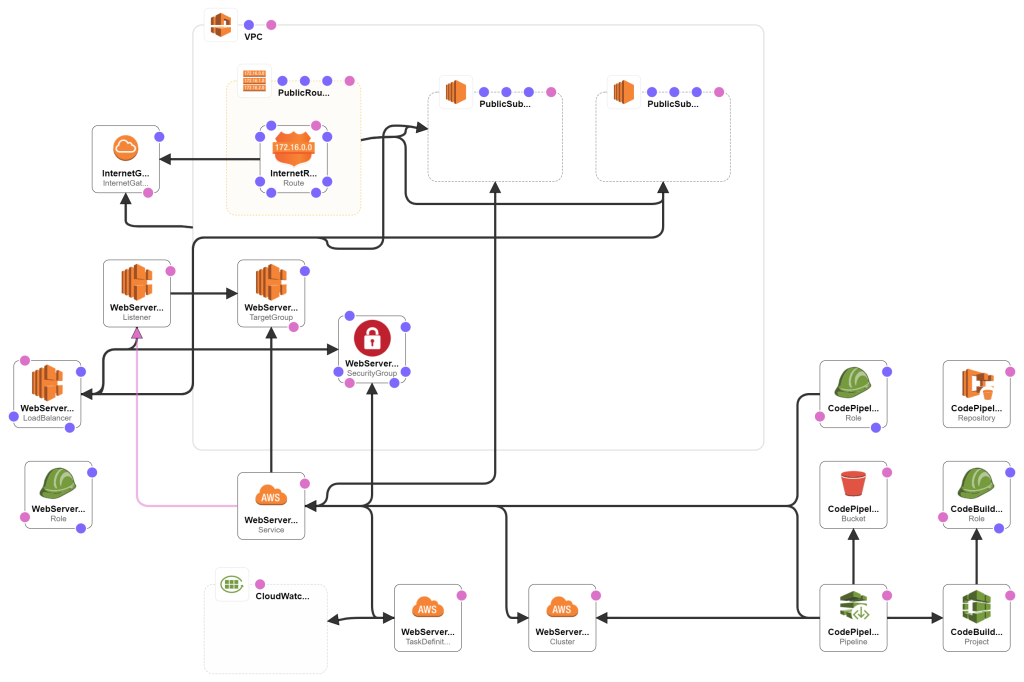
Open 06-container-cloudwatch-template.yaml from previous post and save as 07-container-codepipeline-template.yaml .
Container
We need to add the policy to allow the container service to grab the images from our new Docker registry. Change the WebServerContainerExecutionServerRole like this:
| 1 |
WebServerContainerExecutionServerRole:
|
Add the policy to access the Docker registry. |
- Resource: "*"
|
Add the policy for other required actions. |
Build and Deploy Pipeline
We will need to setup a pipeline to build and deploy our software. Add these resources:
| 1 |
CodePipelineContainerRegistry:
|
The Docker registry to store the Docker images. |
| 2 |
CodePipelineBucket:
|
The S3 bucket to store the source artifacts. |
| 3 |
CodeBuildServiceRole:
|
The IAM Role to allow the CodeBuild project to access the S3 bucket. |
- Resource: !Sub ${CodePipelineContainerRegistry.Arn}
|
And the Docker registry. | |
- Resource: "*"
|
And some other required actions. | |
| 3 |
CodeBuildProject:
|
The CodeBuild project to build the software. |
PrivilegedMode: true |
This is required to build Docker image. | |
Source:
|
The required steps to enable publishing Docker image to the Docker registry. | |
build:
|
The steps to build the software. | |
- |
|
Add the Dockerfile dynamically to the project. | |
post_build:
|
Push the Docker image to the Docker registry. | |
- echo Writing image definitions file...
|
Generate the image definition file so AWS knows how to deploy the Docker image. | |
artifacts:
|
Tell the CodeBuild project how to pack the build artifact. | |
LogsConfig:
|
Store the build log in S3 bucket. | |
| 7 |
CodePipelineServiceRole:
|
The IAM Role to allow the CodePipeline service to access the required resources. |
Policies:
|
It needs to use the source code connection string to pull the source code from the repository. | |
- Resource: !Sub ${CodePipelineBucket.Arn}/*
|
It needs to access to the S3 bucket. | |
- Resource: !Sub ${CodeBuildProject.Arn}
|
It needs to access to the CodeBuild project. | |
- Resource: !Sub ${WebServerContainerExecutionServerRole.Arn}
|
It needs to pass the role to another service. | |
- Resource:
|
It needs to access the container cluster. | |
- Resource: "*"
|
And some other required actions. | |
| 8 |
CodePipeline:
|
This is the pipeline to buid and deploy the software. It will use the S3 bucket created earlier to store all the artifacts. |
Properties:
|
Define where is the source code. | |
- Name: Build
|
Define the build stage. | |
- Name: Deploy
|
Define the deploy stage. |
Update the stack then you should be able to see the CodePipeline. Execute the pipeline and you should get the software built and deployed to the Docker instances.